Request a demo
Please write your contact details and we will contact you soon

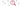
Identifying sensitive data in source code. A proprietary machine learning model is used to reduce the volume of false positive findings.
Searching for sensitive information in source code
Sensitive Data Identification
CodeScoring.Secrets
Problems solved by CodeScoring.Secrets
The presence of sensitive data in the source code, such as passwords and API tokens, can compromise the product by giving an attacker access to the system or user's personal data. CodeScoring Secrets helps to automate the process of searching for such data and significantly reduce the chance of false findings.
12.8 m
90%
1 out of 10
New secrets discovered in public GitHub commits for 2023
Of secrets remain valid 5 days after the leak
Developers accidentally adds a secret to the source code
Code Integrity
Data Security
Leak Prevention
Compliance
Unauthorized Access

Identification of secrets
CodeScoring automatically searches for secrets throughout the code base and conveniently displays them in the UI with reference to the project and the author responsible for leaving sensitive information in the code.
CodeScoring.Secrets key features
We offer a flexible scanning configuration for identifying secrets, provide an ability to manually mark up true-positive and false-positive positives, and improve search quality using our own ML-model.

Scan configuration management
CodeScoring Secrets allows you to use various secret search engines, such as gitleaks, and configure scanning configurations, flexibly adapting the search to the organization's policies.
Assessment of findings using machine learning
Our proprietary machine learning model allows to significantly reduce the number of false positives, reducing the labor costs of security specialists.

True/False Positive markup
The module provides the ability to manually mark up found secrets as true-positive, false-positive, or deleted. Markup is also used to refine the ML model, helping to improve the search quality based on your source code.



Identification of secrets
CodeScoring automatically searches for secrets throughout the code base and conveniently displays them in the UI with reference to the project and the author responsible for leaving sensitive information in the code.
CodeScoring.Secrets key features
We offer a flexible scanning configuration for identifying secrets, provide an ability to manually mark up true-positive and false-positive positives, and improve search quality using our own ML-model.

Scan configuration management
CodeScoring Secrets allows you to use various secret search engines, such as gitleaks, and configure scanning configurations, flexibly adapting the search to the organization's policies.

Assessment of the findings using ML
Our proprietary machine learning model allows to significantly reduce the number of false positives, reducing the labor costs of security specialists.

True/False Positive markup
The module provides the ability to manually mark up found secrets as true-positive, false-positive, or deleted. Markup is also used to refine the ML model, helping to improve the search quality based on your source code.

Supported systems

















Request a demo
Here you can request a demo, check pricing, get an educational license, or partner with us


